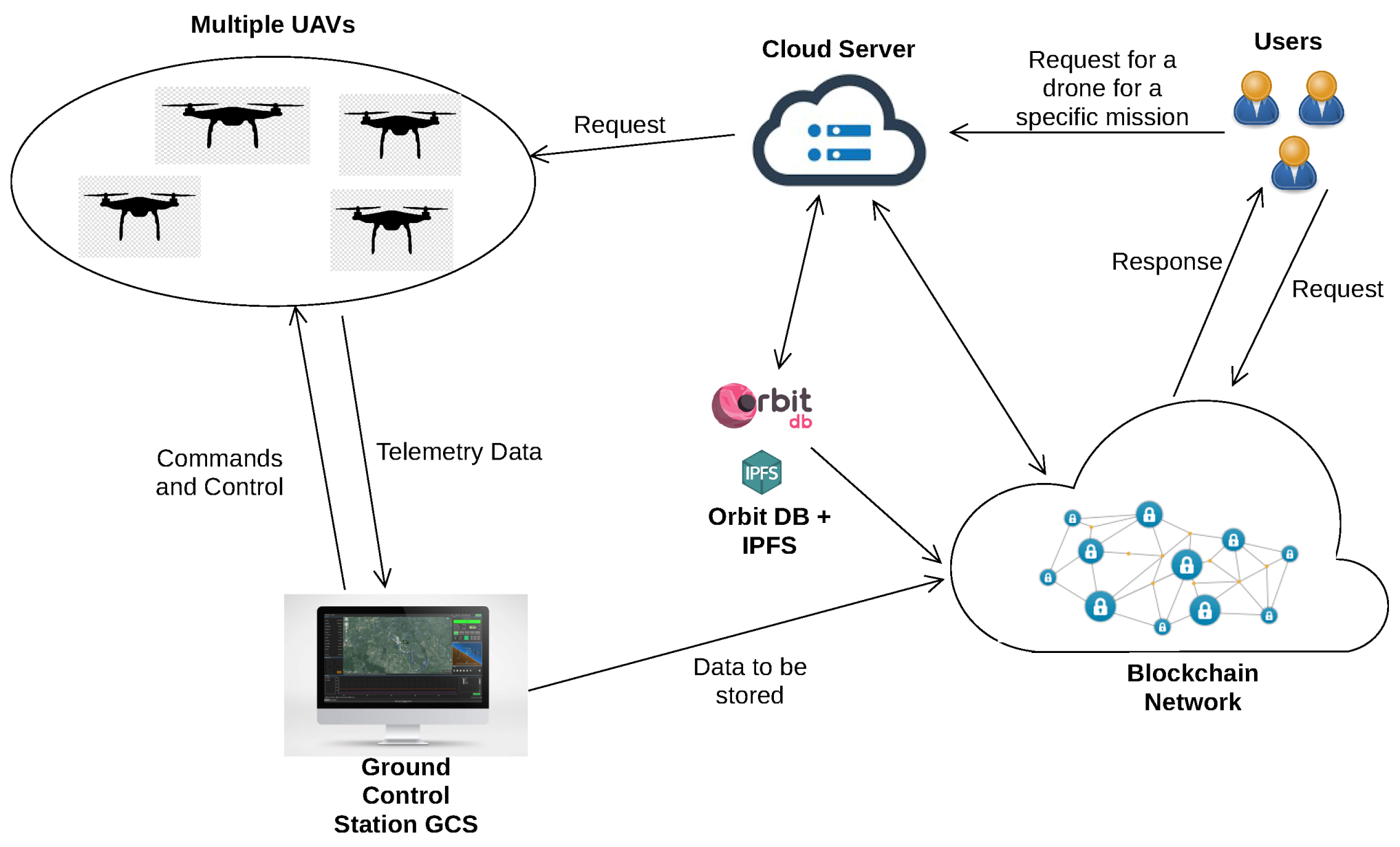
Sensors | Free Full-Text | UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones

Enterprise data breach: causes, challenges, prevention, and future directions - Cheng - 2017 - WIREs Data Mining and Knowledge Discovery - Wiley Online Library
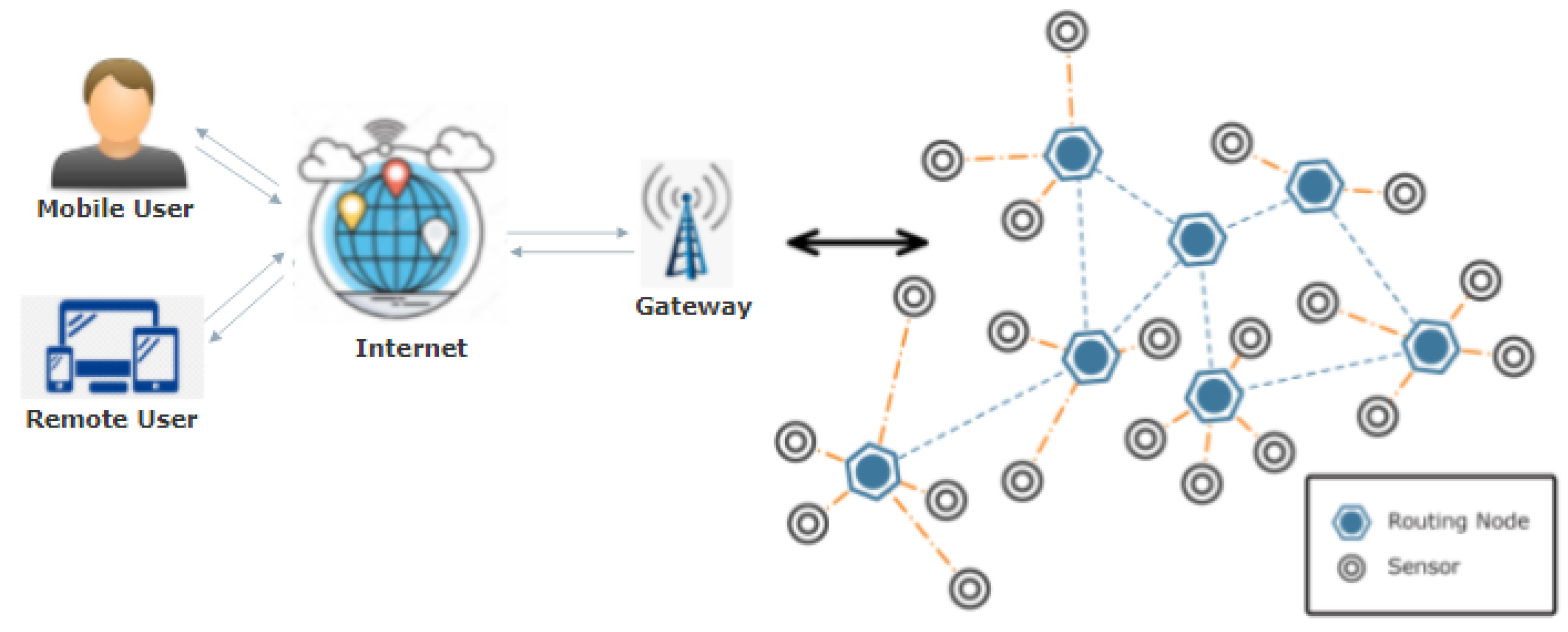
Sensors | Free Full-Text | Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review

Combating Information Manipulation: A Playbook for Elections and Beyond | International Republican Institute
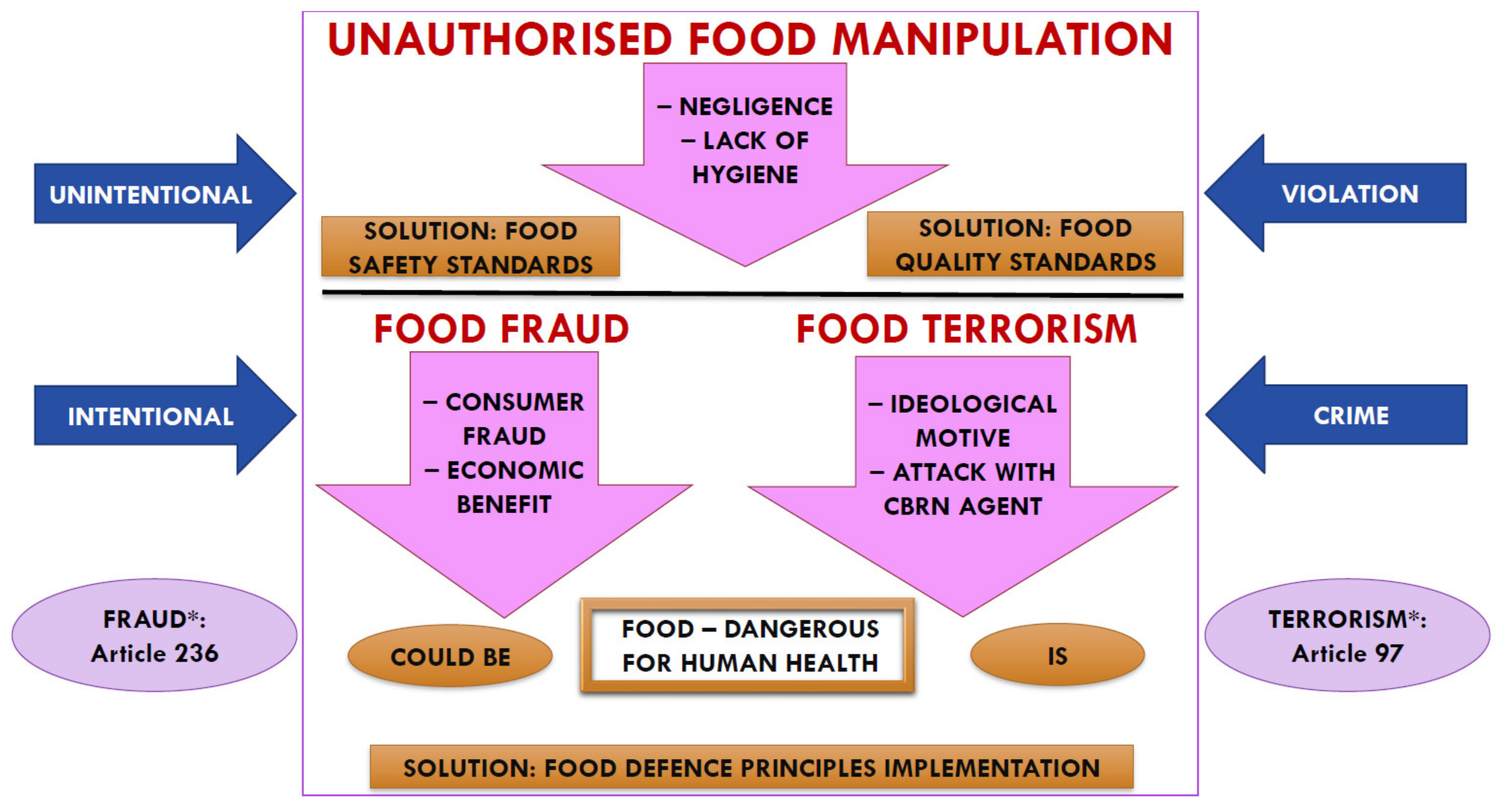
Foods | Free Full-Text | Unauthorized Food Manipulation as a Criminal Offense: Food Authenticity, Legal Frameworks, Analytical Tools and Cases

Fundamental Mechanisms of Regulated Cell Death and Implications for Heart Disease | Physiological Reviews
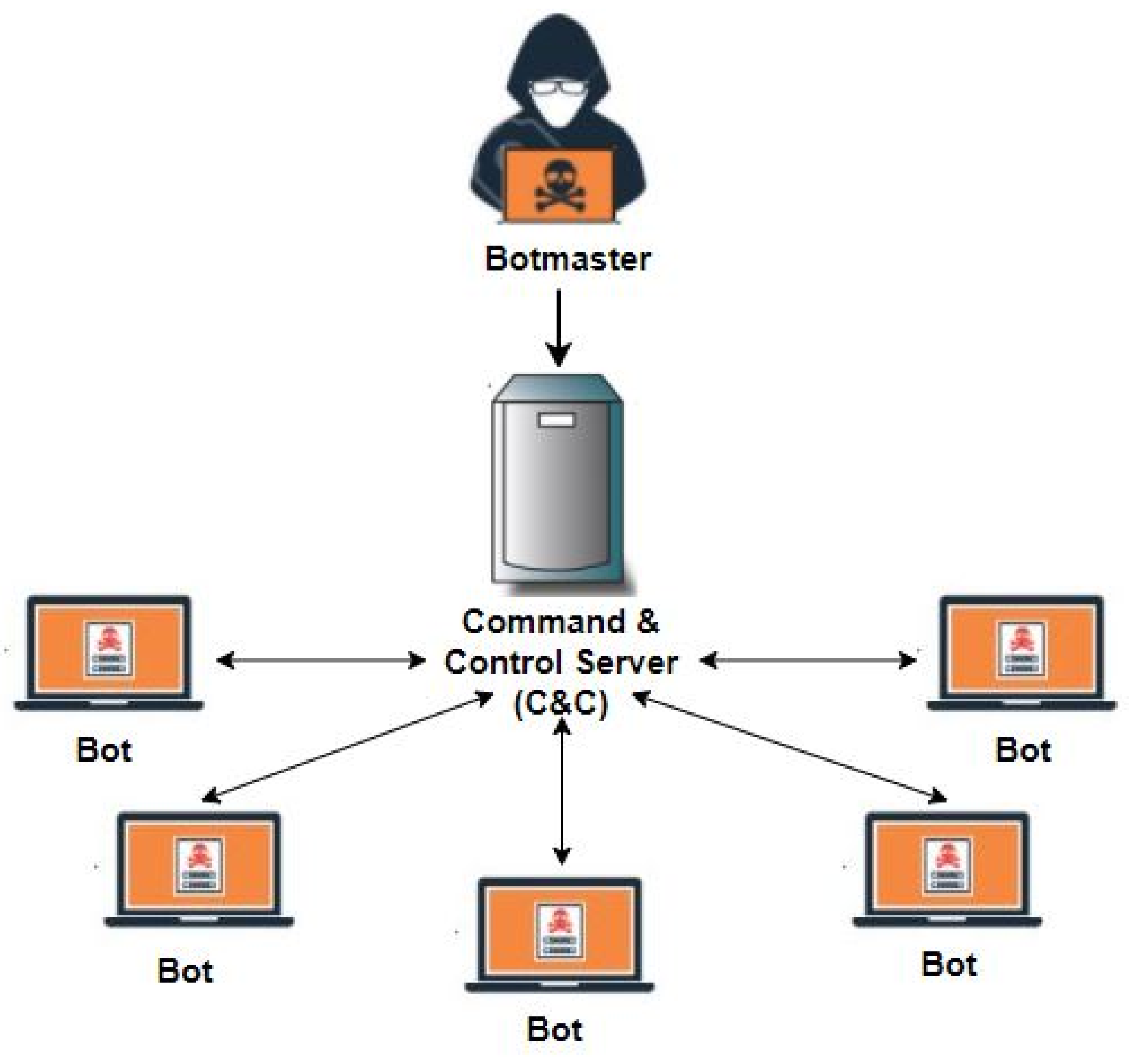
Symmetry | Free Full-Text | Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review